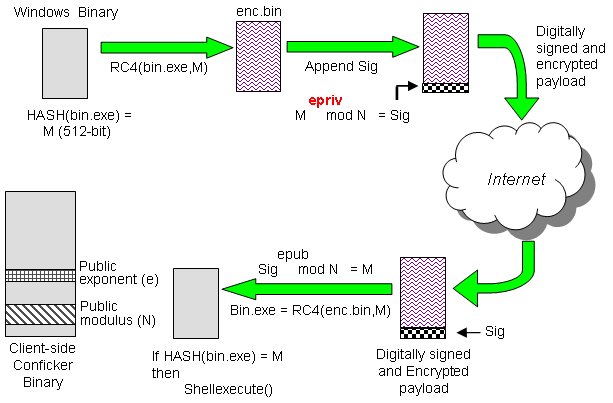
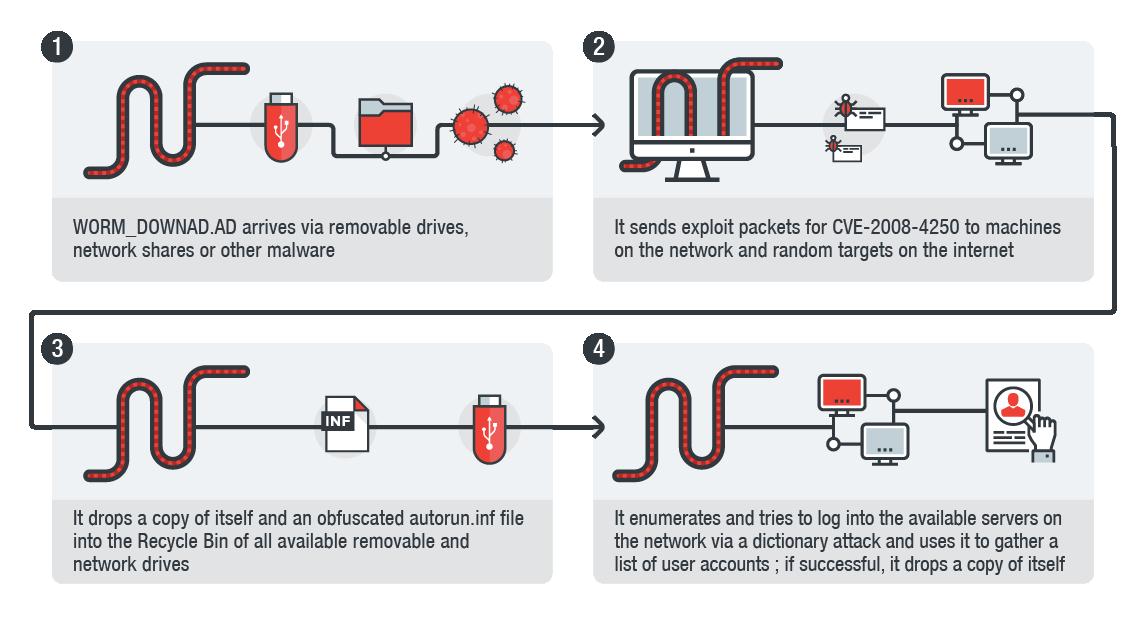
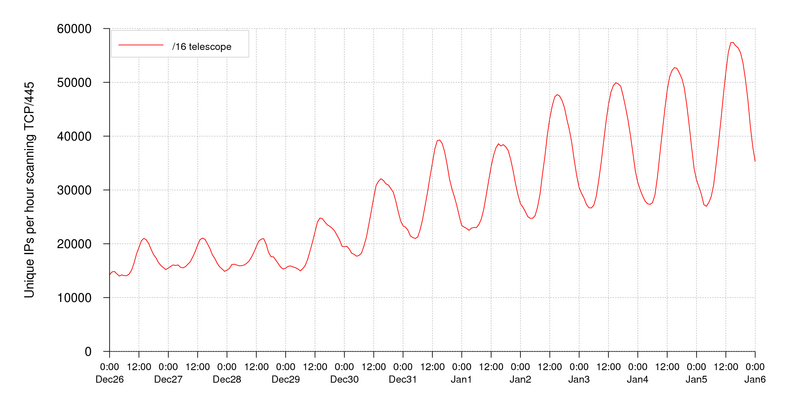
Ace Info About How To Detect Conficker On Network

If you are running linux, nmap may already be installed.
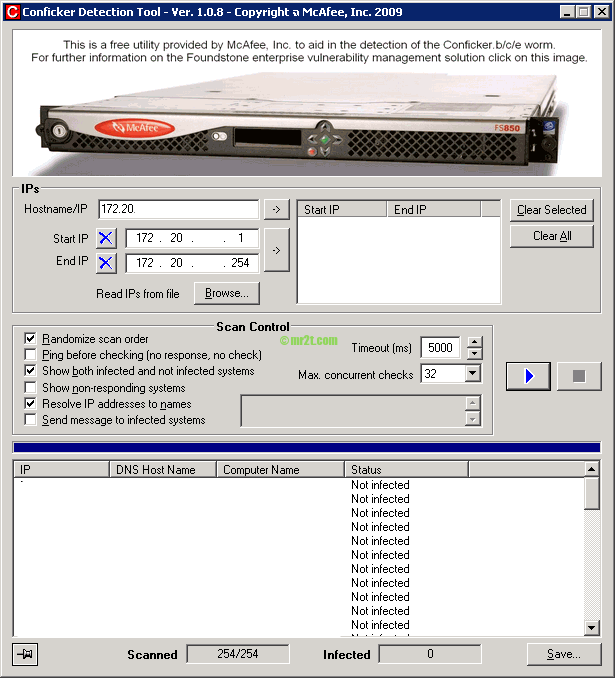
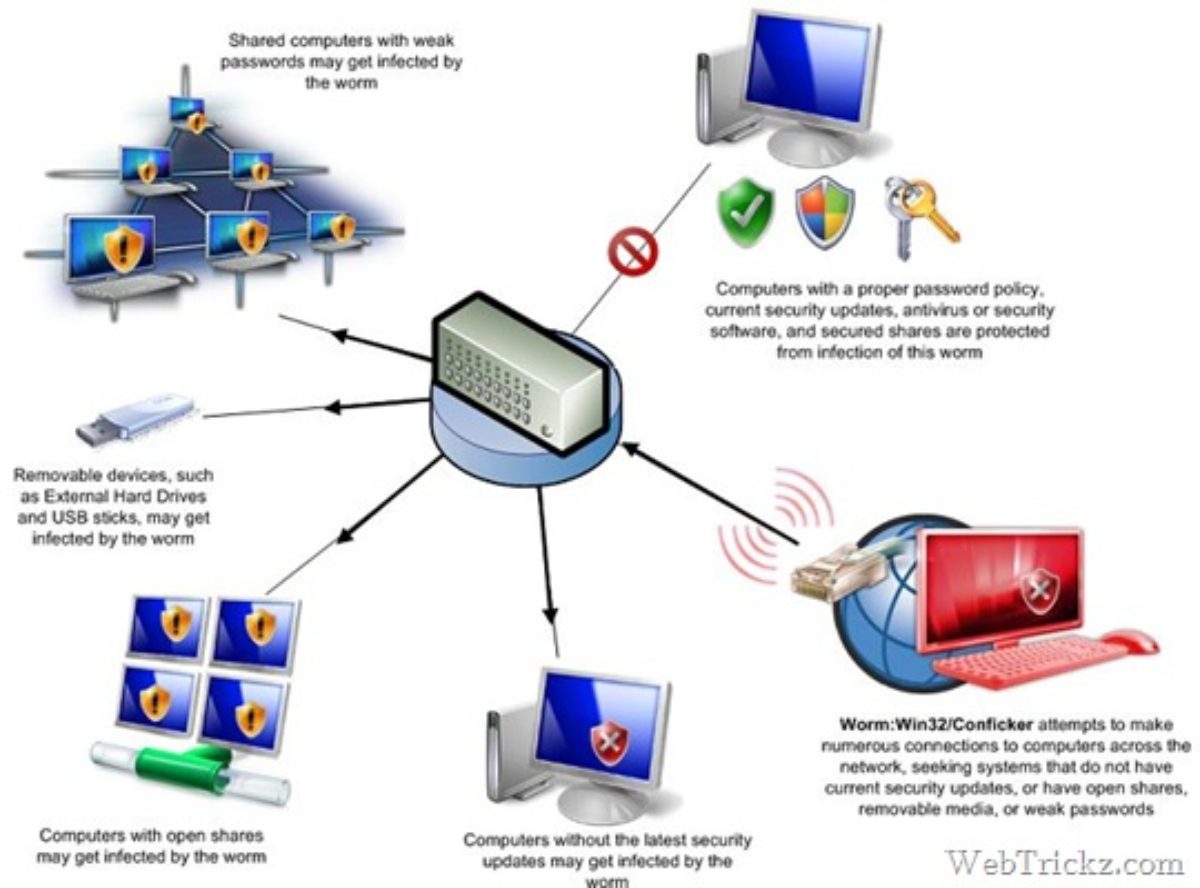
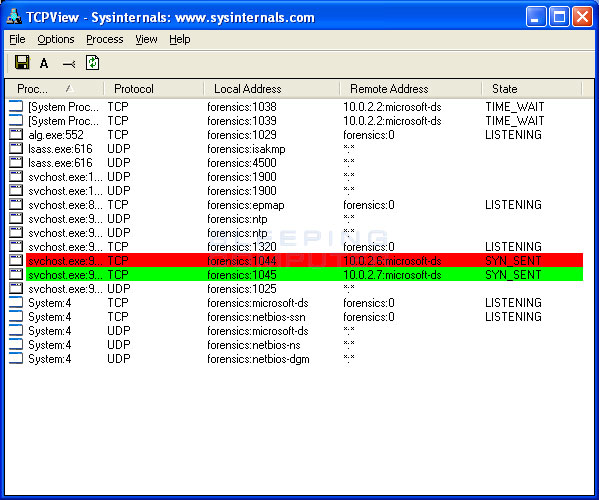
How to detect conficker on network. This report details the time (utc or gmt unless stated otherwise), protocol, source address and port, and destination address and port of connections related to conficker infections. There are three options in the above command to help cut down on the amount of work nmap has to do per host: March 30, 2009 | 1 min read nessus plugin # 36036 performs a network based check for windows computers infected with a variant of the conficker virus.
The latest version of nmap has the ability to detect all (current) variants of conficker by detecting the otherwise almost invisible changes that the worm makes to the port 139 and port 445. | check 1 (port 44329/tcp): When there's a large number of traces of malware or worms, for example conficker, that have infected a computer, the only remedy may.
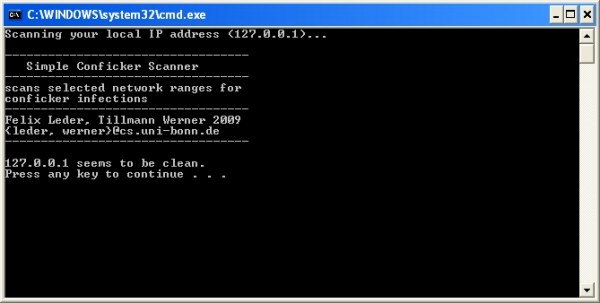
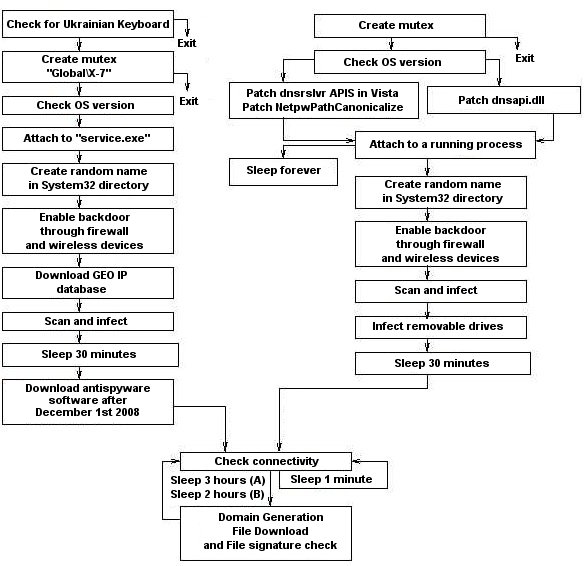
I figure everyone is good and ready for tomorrow but just in case you want to double check or still need to scan your network here is a quick and easy method with nmap. If you suspect that a conficker infection is in place on computers in your network, you can use the free utility nmap to detect infected clients using the following commands: Given that one conficker variant installed additional malware, the end goal seemed to be monetary gain by selling fake security software and creating a botnet to distribute spam.
= [ (30 × 3)× 2] × [ (80 × 3)× 1] × [ (10 × 5)× 1.5] = 3,240,000 units 3 since this portion of the attack is disjoint with the other 4 portions (i.e. You can download the latest nmap for os x. The latest nmap release can test windows machines for conficker infection.
Felix and i had a discussion with dan kaminsky about the. After being infected i tried using the enigma conficker remover tool, which first cleaned my system, the problem is that after i got connected to a computer on the network or.